Points taken from article:
- Android 15 is adding a built-in mechanism to protect your device from “juice jacking” attacks.
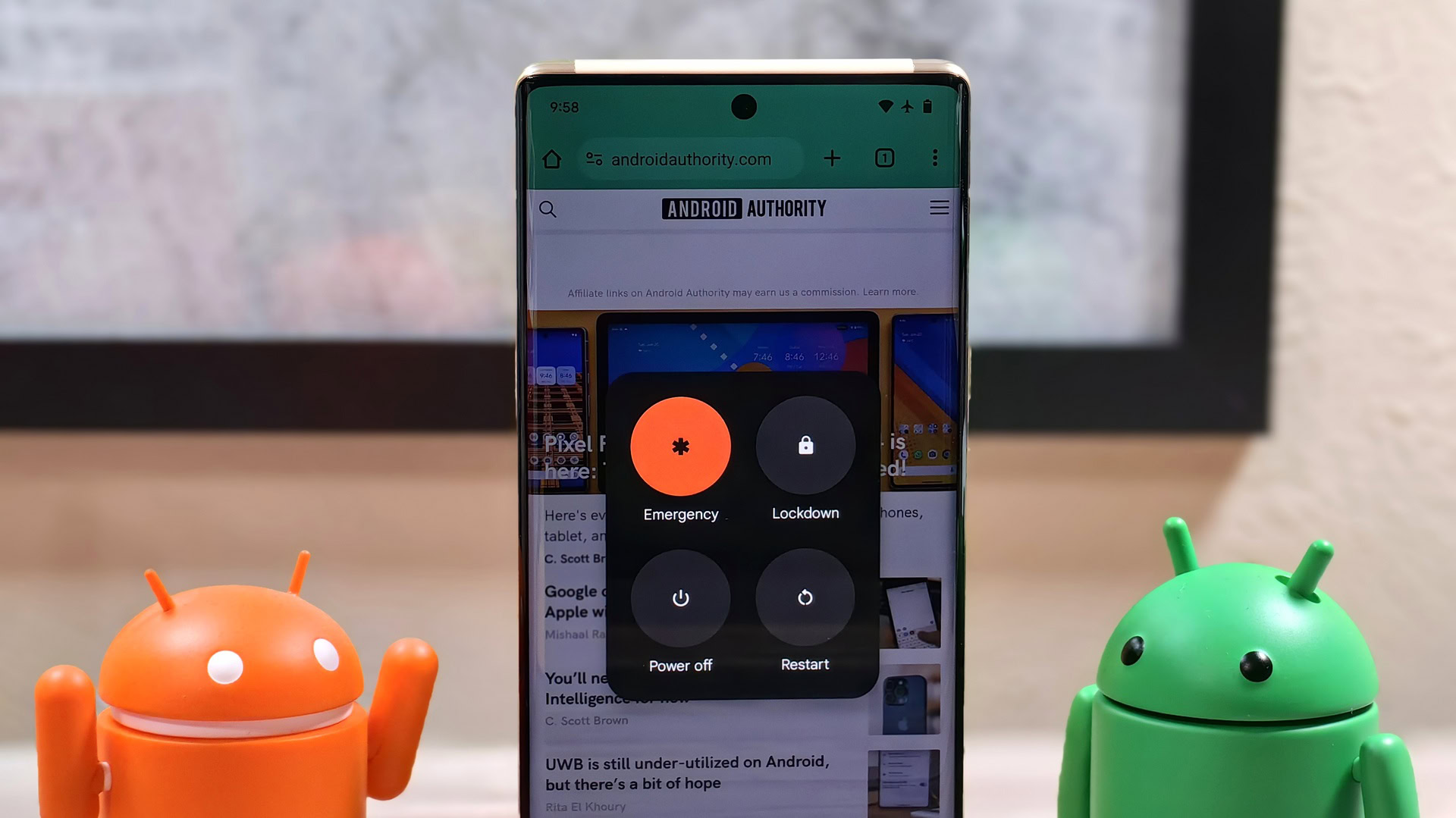
- Charging will be allowed when lockdown mode is enabled in Android 15, but USB data access will not.
- Juice jacking is a largely theoretical problem you don’t really need to worry about, but it’s still nice that Android will protect you against it.
You certainly don’t want anyone jacking your juice without permission.
That’s why I use a USB condom.
Just in case you are joking (or people think you are) those do exist. Basically a dongle with only the power pins on each end.
This is only useful if you’re not using your own cable. Otherwise you can simply use a “power only” cable.
But better use the condom dongle for only $59 !
5.49€ for a USB-C to USB-C condom, and I can’t even find a USB-C charge only cable.
Personally, I plug a power bank into the public port and charge my other devices through it. But if an AC outlet is available, that’s all moot anyway.
Your devices will charge slowly or potentially not at all
There are some that do power negotiation on the input side, and then power negotiation on the output side so you can have your cake and firewall it too.
Well im more worried about people juiceing my phone in a literal sense XD
juce jacking would have to be a targeted attack, as it has to be very specific in unlocking and stealing data.
Not necessarily, if you find an exploit that allows you to install malware without user interaction, Mactans famously did that for an older iOS version.
I’d still argue that making good use of such an exploit and rolling out the necessary, physical infrastructure does not have a great cost/reward ratio.
Ios is funnily enough more prone to such attacks as its always the same chipset with always the same OS. Android in comparison has hundreds of different OS versions and many different chipsets.
Just put up a free charging station or an outlet with a USB port in a hotel and you got yourself free USB connections to phones.
I can never bring myself to connect to those things.
Sure. But the number of targets you could acquire there is miniscule compared to simpler delivery mechanisms, via a malicious app download, for example, and you have larger costs (hardware) and added risks, e. g. being captured on CCTV during installation.
That’s why I said, the cost/reward ratio is really off.
Why? I have never heard of this happening
I don’t use my phone for that, I swear!
This can also be practical in places where the police can force you to unlock your phone with biometrics but not with the PIN.
Ever since I’ve seen the police here force people to delete the videos of them abusing citizens, I have been very wary of biometric identification.
So far my ‘emergency’ procedure would be to restart my phone, as it’s asking for a PIN after a reboot.
LineageOS has been doing this for a year or so already.
Same on GrapheneOS :)
It’s smart! Do not expose logic without first supposing an appropriate level of trust. Software can have errors.
Pixel UI seems to have it too, but does that not prevent data transfer?
How is this different from current Android
Lockdown mode was introduced in 2018’s Android 9 Pie release as an optional feature users could add to their power menu. When enabled, lockdown mode hides notifications and disables all forms of authentication except for the user’s primary authentication (PIN, password, or pattern). In Android 12, Google made the lockdown mode toggle appear by default in the Android power menu, though some OEMs hide it or offer their own, similar version of the feature elsewhere.
Android 15 will further restrict USB access in this mode to help defend against attacks.
Don’t you already need to unlock the phone to change USB protocol?
Yes, but the data pins are still connected and talking to some software. That software can have vulnerabilities.
It’s more secure to allow no communication whatsoever, whereas it’s extremely hard to prove that any software is free of vulnerabilities.