Apple quietly introduced code into iOS 18.1 which reboots the device if it has not been unlocked for a period of time, reverting it to a state which improves the security of iPhones overall and is making it harder for police to break into the devices, according to multiple iPhone security experts.
On Thursday, 404 Media reported that law enforcement officials were freaking out that iPhones which had been stored for examination were mysteriously rebooting themselves. At the time the cause was unclear, with the officials only able to speculate why they were being locked out of the devices. Now a day later, the potential reason why is coming into view.
“Apple indeed added a feature called ‘inactivity reboot’ in iOS 18.1.,” Dr.-Ing. Jiska Classen, a research group leader at the Hasso Plattner Institute, tweeted after 404 Media published on Thursday along with screenshots that they presented as the relevant pieces of code.
Law enforcement shouldn’t be able to get into someone’s mobile phone without a warrant anyway. All this change does is frustrate attempts by police to evade going through the proper legal procedures and abridging the rights of the accused.
Yep! The police, being fascists, HATE this.
well it’s kind of a selling point. I’m just too used to using android, though.
Edit - there’s something for that too, cool!
You can enable lockdown mode. It forces the next unlock to ignore biometrics and require a pin, which police cannot force you to divulge without a warrant. Once enabled, you get a “lockdown mode” option in the menu when you hold down your power button.
If you haven’t done this and need the same ability IMMEDIATELY: reboot, or just shut down
Every first boot requires pin same as lockdown
Also: set a nonstandard finger in a weird way as your finger unlock if you wanna use that, then theyre likely to fail to get that to work should you not manage to lock it down beforehand
Finally: there are apps that let you use alternate codes/finger unlocks to wipe/encrypt/reboot the device instead, allowing you to pretend to cooperate with the cops up until they realize they got played
IANAL, but I’d be very careful about wiping the phone like that. Sounds a lot like destruction of evidence…
Gotta prove there was evidence on the phone in the first place, which would take forensic work to do and be not worth the work in the majority of cases
Plus it would annoy them, and that’s the real goal here
I imagine that would be one hell of a story to tell Bubba when they decide to lock you away for whatever false charges they can pin on you.
When the cops are about to fuck you like this… Defending yourself is the priority lol wtf clown take is this.
sounds like the point
It’s not destruction of evidence though because without a warrant the information on the phone isn’t evidence, it’s just stuff on a phone. Stuff which is your stuff and you have every right to delete it whenever you want.
They would actually have to arrest you and acquire a warrant, try it to getting you to unlock the phone for it to be “evidence”.
The police would have a very hard time in court saying that there was evidence on the phone when they can’t produce any documentation to indicate they had any reason to believe this to be the case. Think about the exchange with the judge.
“Your honor this individual wiped their phone, thus destroying evidence”
“Very well, may I see the warrant?”
“Yeah… Er… Well about that…”
It doesn’t matter what the police may think you have done, if they don’t go via the process the case will be dismissed on a technicality. They hate doing that but they don’t really have a choice.
So many words to explain how you literally have no clue about how the law works.
In what way am I wrong then?
Also: set a nonstandard finger in a weird way as your finger unlock if you wanna use that
I actually do this. 3 wrong attempts and the phone requires a password.
I consider it a very light measure and not something to rely on alone, but it’s a bit of a no-brainer for how easy and unobtrusive this is.
Although lockdown mode is a good step and helps defend against biometric warrents, it does not wipe the encryption keys from RAM. This can only be achieved by using a secondary (non-default) user profile on GrapheneOS, and triggering the End session feature. This fully removes the cryptographic secrets from memory, and requires the PIN or password to unlock, which is enforced through the StrongBox and Weaver API of the Titan M2 secure element in Pixel devices.
You can use GrapheneOS, a security-focused version of Android which includes auto-reboot, timers that automatically turn off Wi-Fi and Bluetooth after you don’t use them for a certain period of time, a duress PIN/Password that wipes all the data from your device after it’s entered, as well as many other incredibly useful features.
It’s fully hardened from the ground up, including the Linux kernel, C library, memory allocator, SELinux policies, default firewall rules, and other vital system components.
graphene is ONLY for select Google pixel phones though. I wish this was made much clearer by the team and advocates.
its a real shame because pixels, although big in the USA are typically a minority of most android ecosystems elsewhere, and bootloader hijinks keep some perfectly capable phones from being easy to switch over to, even if they were supported.
Even on samsungs, which are much better for flashing than they used to be - my options on a year old flagship for a decent ROM are pathetic compared to the old days.
so I would really love to use graphene, and go back to an open source ROM without crap on it, but pixels are such a bottom tier phone for their price in a lot of places, as much as I really really want the project go gain traction for their transparency and objectives.
but pixels are such a bottom tier phone for their price in a lot of places
Not sure what you mean, you can get a used Pixel 6a for 120 EUR, which will continue to get updates for another 2.5 years. Show me another phone with such a great value proposition. There’s a website that calculates how much each Pixel would cost you monthly (it’s basically just price divided by update lifetime): https://pixel-pricing.netlify.app/
There are some really good deals, and I’d rather pay a little more for a phone that can actually be used privately, instead of buying some cheap Chinese, spyware-infested garbage that will fall apart after 2 years, and never gets any security updates.
Not sure what you mean, you can get a used Pixel 6a for 120 EUR, which will continue to get updates for another 2.5 years. Show me another phone with such a great value proposition. That’s exactly my point, outside of the EU and north america, you’re just very unlikely to find that scenario. I don’t want to doxx myself here, but the going rate for the phone you mentioned is at minimum 300 euro equivalent - comparable flagships significantly cheaper. I have nothing against Pixels specifically - before the re-brand, I had nearly every Google Nexus phone ever made, and they were all amazing. They’re just not acceptably priced in all markets for what they are, even used.
I’d argue however that there’s much more to android than either Pixels OR chinese spyware crap - Samsung, Sony, and LG aren’t always perfect, but often make very good products that if running a custom ROM, are every bit as secure as any pixel, while the hardware of pixels is generally a bit worse, but compensated for with better software optimisation. Buying into a false dichotomy that there is only one good android manufacturer puts us no further ahead than apple fanboys beholden to a largely good, but sometimes flawed ecosystem.
My ideal is that development can expand to other mainstream brands and OEMs, and that the interest in the graphene/ROM community picks up steam more broadly, rather than being siloed into pixels alone, and bound to the fate of google-specific hardware going forward.
I’m the only guy in my (small) friend group who still used pattern code instead of fingerprint so I take that to mean my phone is by default more difficult to break into than most. Giving my fingerprint to a giantic tech firm has always seemed like a bad idea so I never did. Though the fingerprint reader acts as a power button too so who knows if they’ve scanned it anyway.
Afaik the fingerprint is stored on dedicated hardware on your device, it never leaves your phone and cannot be “read”
Patterns are too easy to breach via brute force is my understanding like comically easy
Any modern phone os locks to pin after 3 tries.
Now depending how good they are, it’s often possible to guess it by looking at the smear patterns on the phone.
Most phones aren’t letting you try more than 5 attempts before you’re locked out. You can even set it up to erase after the attempts
Most attacks are done offline. If they clone the encrypted partition, they can brute-force as fast as they want. Pin lockouts can’t protect against that.
You are showing a limited understanding of law enforcement’s capabilities for brute force attacks.
They make an imagine ofnthe device and then brute force it so you better have that 16 character password.
Makes sense, but in that case, why do law enforcement even care if the OS reboots itself if they already have a copy of the encrypted contents?
properly passworded os still has vulnerabilities that they want to exploit.
OP is just one vulnerability closed.
You mentioned wipe feature after fialed tries, thats a tactic that a person with serious threat model can use but cops go a work around it.
All current stock Samsung phones can do this too, BTW.
Well, when you confiscate a piece of paper, even without a warrant to read it you can do that physically when it’s in your possession, and it’s part of the evidence or something, so everyone else can too, so why even fight for that detail.
They just pretended it’s fine with mobile computers.
I thought that “fruit of a poisonous tree” is a real principle, not just for books about Perry Mason. /s
So - yes. It’s just really hard to trust Apple.
To confiscate anything, unless it’s lying openly, you need a warrant.
If a cop sees an unlocked phone with evidence of a crime on it, that doesn’t need a warrant. If it’s locked and they only have the suspicion of evidence, they need a warrant. Same as with entering a building or drilling a safe.
Is analogy with people in (very quiet) places who don’t lock doors to their homes correct? Then it’s as if the door is not locked, a cop doesn’t have to ask permission (or warrant)?
No. Even if a house is unlocked, the fourth amendment guarantees “the right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures”.
What constitutes “unreasonable”, is of course, up to a judge.
If a cop can look in your window from the porch and see a meth lab, yeah, they’re going to come back with a warrant, mostly because they can’t just pick up the house and take it to evidence. If your phone is lying unlocked, and they see something obviously criminal on the screen, they’re going to take it right then and there.
That’s what I meant. Phones should be treated similarly to houses.
Seems like he’s saying they are. If they see something criminal on the phone then it’s not an unreasonable seizure.
That argument sounds great until you consider that a piece of paper won’t contain almost the entirety of your personal information, web traffic, location history, communications. You may say you could find most of that pre computer era in someone’s house, but guess what you would need to get inside and find those pieces of paper…
It’s not an argument, just a thought.
They usually do have a warrant or it was seized lawfully.
This is about keeping them out even when it’s lawful.
Lawyer. Not true.
Example: An officer pulls someone over and suspects them of something arrestable. Then says “Do you want me to get your personal belongings from your car?”
Any person agreeing to this allows them to hold your phone as evidence indefinitely in the US now.
That’s all lawful.
They can search you and the area when arrested. They can search the car if they have probable cause that evidence will be in the vehicle
I said have a warrant or seized lawfully, not nust have a warrant.
Edit: I didn’t even write what I said I said correctly. Corrected it lol.
Seized or not, they can not force you to unlock your phone via pin without a warrant. They can only force you to use biometrics.
Right, but this is about them bypassing you entirely.
They don’t need your fingerprint or pass code if they can bypass it themselves. This feature protects you when they’ve seized it lawfully which can be for many reasons.
Or even if they’ve seized it unlawfully. Or if it’s been stolen by a regular thief, a cybercriminal, the mafia, or a cartel.
I’m not sure how much it would actually help for a regular thief.
This is about protecting it against more sophisticated attacks. But the rest probably have those means if wanted.
It is their job to find evidences, not my resposibility to provide them.
I’ve never said otherwise.
It’s their job to find a way to hack into the phone.
This feature makes that even harder.
Other people answered, but to your point, in some cases THEY CAN compel without a court order.
Biometrics don’t conform to certain laws, and it gets even more complicated if you’re entering the US through customs. They can practically hold you indefinitely if you don’t comply. Whether you have legal representation is sort of an after thought.
The police can engage in rubber-hose cryptanalysis. In many countries, it’s legal to keep a suspect in prison indefinitely until they comply with a warrant requiring them to divulge encryption keys. And that’s not to mention the countries where they’ll do more than keep you in a decently-clean cell with three meals a day to, ahem, encourage you to divulge the password.
That’s what you need distress codes for.
Destruction of evidence is a much different crime.
I would suspect it’d no longer be legal to hold them indefinitely and instead at best get the max prison sentence for that crime instead.
A us law website says that’s no more than 20y as the absolute max, and getting max would probably be hard if they don’t have anything else on you.
You’d have to weigh that against what’s on the device.
Also, even better if the distress code nukes the bad content, and then has a real 2nd profile that looks real, which makes it even harder to prove you used a distress code.
In most cases, destroying evidence will result in an adverse inference being drawn against the accused. It means that the court will assume that the evidence was incriminating which is why you destroyed it.
IT support everywhere sigh in satisfaction
GrapheneOS also has this. Not sure stock android includes it.
It does not. I don’t have it on my Pixel 6. From other people’s comments, it sounds like Samsung and other OEMs have added their version, though.
Yeah, can confirm Samsung has this. I have auto reboot configured.
Where would I find that setting? I have an S22 Ultra and I can’t seem to find it. Unless my phone has fallen out of support…
It’s under device care -> auto optimization in settings. You can also just search “restart” in settings and it should pop up.
Found it, thanks!
Thanks, didn’t know of this function. In my A50s it’s under Battery and Device Care
that makes me think that it’s a different feature, and it reboots the phone every x hours regardless if it was unlocked
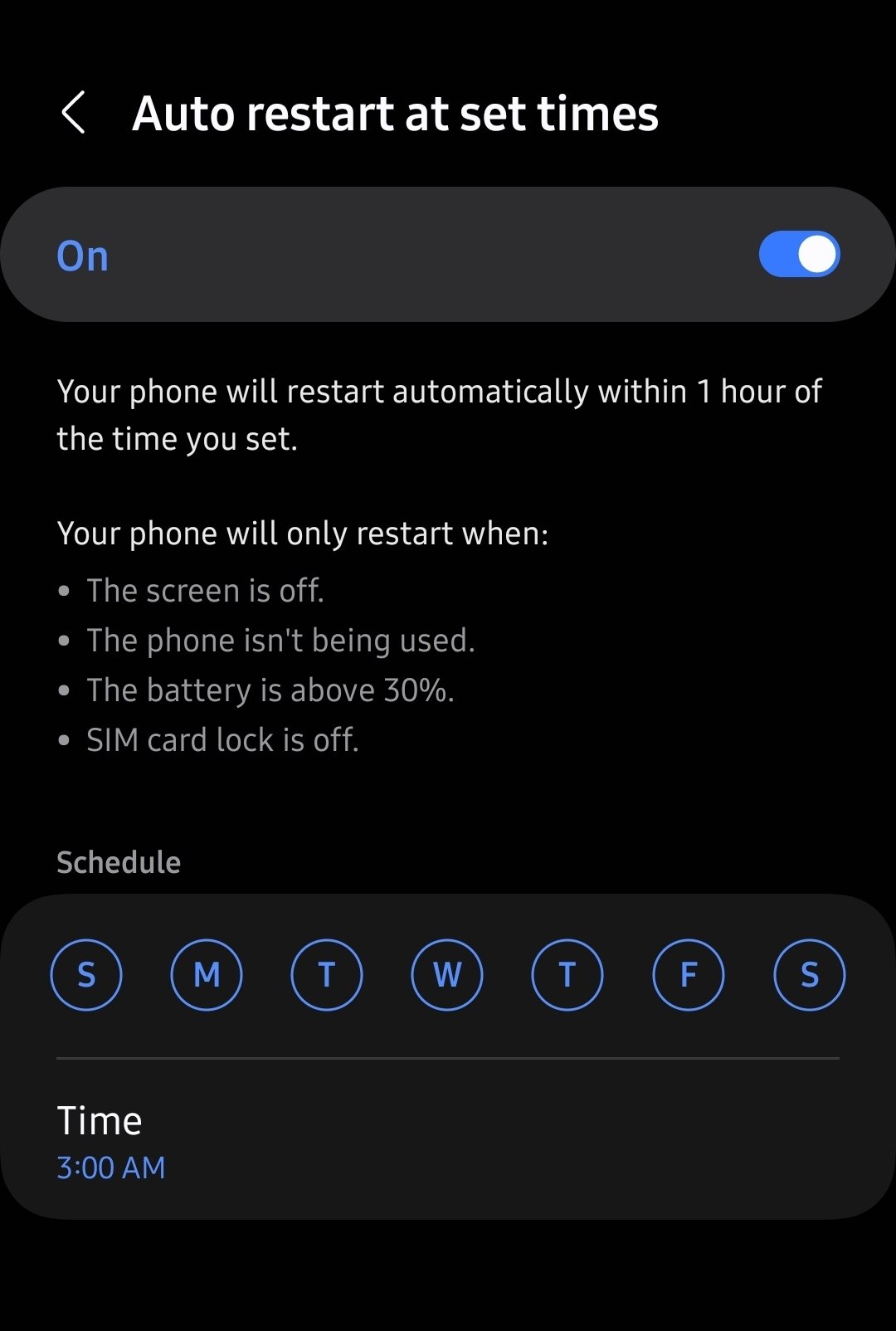
so this is a restart-on-schedule feature that can skip a restart on certain conditions
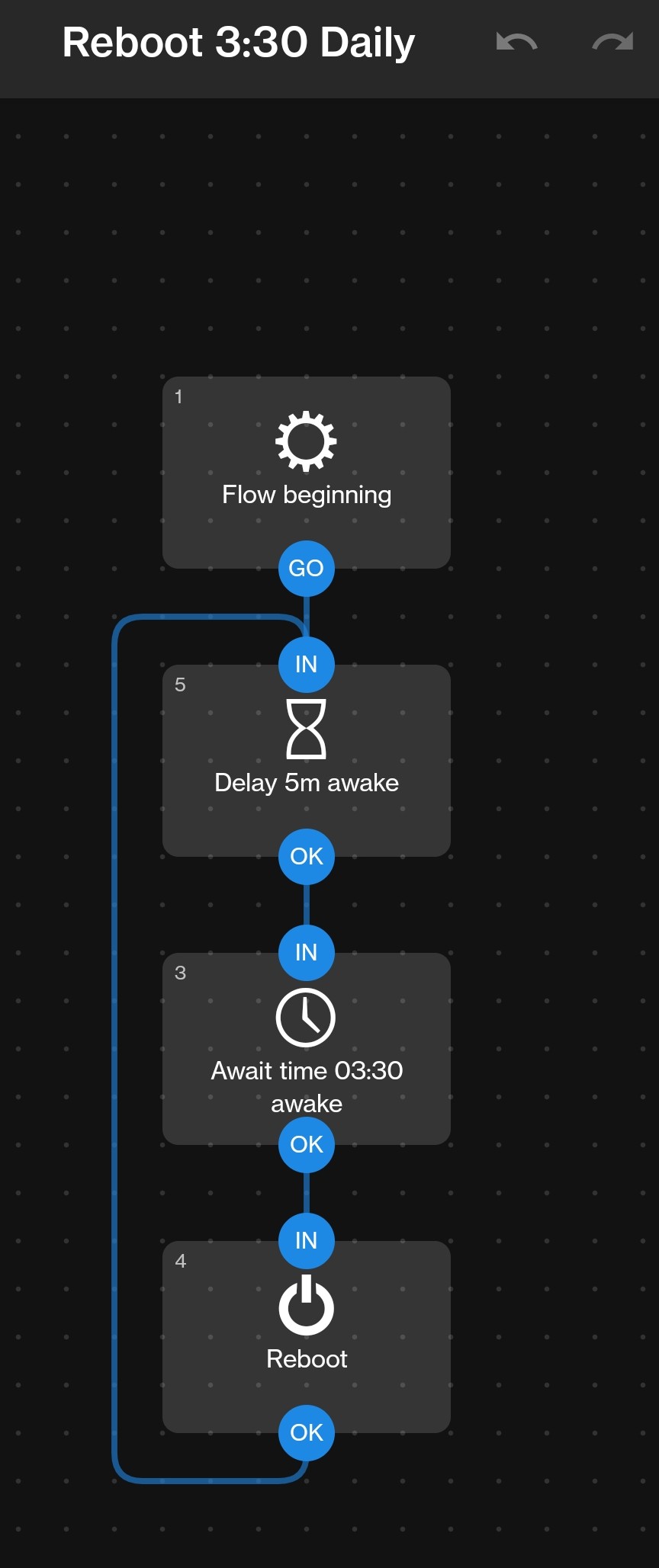
I’ve added this function manually using Automate (https://play.google.com/store/apps/details?id=com.llamalab.automate).
You can trigger it to reboot on inactivity using some advanced parameters, but I’ve simply set it up to reboot at 3.30 AM every day, that way it’s also clearing the cache.
This is how it looks like - the 5 min wait timer is to prevent a reboot loop if the phone is still booted up at 3.30 again.
That seals the deal for me on rooting my pixel. I’ve been hesitant about rooting ever since I bricked an extra galaxy s3 and nearly bricked my (main device) Verizon galaxy s5
If you have a factory pixel, you don’t need to root. You can unlock bootloader and install a rom that has it (calyxos or grapheneos I know have them). You can root, but you don’t have to.
Putting graphineos onto my pixel was the easiest thing I’ve done in a long time, the installer is just pressing buttons and waiting for the next button to be ready pretty much.
How does it work for stuff like bank apps? Do they freak out about it?
And does it require unlocking the bootloader? I prefer to keep mine locked if possible.
My bank app works fine and I can use the NFC chip for payments as well, it might pay to search up your bank name and graphineos to see if anyone’s had an issue, that’s what I did to make sure.
You have to unlock it to install but once installed they prefer you lock the bootloader back up again.
Same question as catloaf but with less ambiguous things like banks: does Netflix, safety net, fox sports Australia and Google pay work with graphene os?
My bank apps all work (though YMMV.) Ticket app worked (AXS.) I haven’t actually used google pay or google wallet for anything to know if they work.
Authy is the only miss I’ve found and it wouldn’t have mattered if i hadnt been caught in the midst of migrating to another app for that when they decided to be assholes.
Google wallet doesn’t work at all, but if your bank offers its own NFC payment system then that should work.
The only app that I’ve had an issue with was uber, that refused to install from either play store or aurora store, but beyond that I haven’t had any issues. Just search graphineos and the app you want to check, or check out their forum.
GrapheneOS is the easiest ROM install bar none. Get the en browser (needs to be chrome-based) to the install url, hook the phone cable, and let it run. It’s super straightforward. It’s not rooting though, you don’t get root access by default.
Wow things sure changed about Android roms! I still remember how difficult it was to try to simply install a rom through Knox
samsung devices are still a different beast, they have their unique little everything and the standard tools don’t work there
You can add the function easily using https://play.google.com/store/apps/details?id=com.llamalab.automate, no root needed.
It’s either root or having access to my bank accounts. 🙄
Change banks.
Have a 20 year mortgage with that bank so no.
calyxOS has it too.
Didn’t know that. Just been manually rebooting. This is is much easier and more secure. Thanks!
Sure, glad to help. We need every bit of help against the powers that be at this point.
Agreed! When everything is actively against us, we must band together against everything.
Fighting centralized power with decentralized approach!
It does, labled “Auto Restart”, but only when “preformance issues detected” or time specified. Apple is quite late on this feature.

This is rebooting for a different reason. That auto reboot just kind assumes that the software on your phone sucks and it needs to reboot to stay running fast.
Graphene and now iOS auto reboot for security/privacy reasons.
The end result is the same though. First phone unlock is the one a bad actor can’t get through.
It’s not the same.
On an iPhone it’ll reboot after X hours of no use. That means it could go months without rebooting and the day after it’s in police hands it reboots.
The feature you’re talking about would need to be set to reboot every day at a specific time. Now you personally have to deal with that. Also until you unlock the phone as well there could be reduced functionality making it annoying.
Very different.
Not that hard to deal with honestly. Rebooting at night which I’m sleeping does not reduces any functionality, cuz I’m not using it. If someone needs to find me during the night he better call me cuz I won’t wake up by notification which is also suppressed by DND. Yeah it is not design for security but a solution better than none.
Furthermore, rebooting the device periodically is good for security, especially for non-persistent fileless malware.
on GrapheneOS it is labeled auto reboot and it specifically says “automatically reboot device if it hasn’t been unlocked in xxx hours” with a default of 18.
This is clearly the Samsung interface and thus not stock Android. Doesn’t even really look like the same feature.
Does that stop alarms from going off in the morning?
depends on your phone. at first encryption was done in an all-or-nothing style, so system startup couldn’t complete without a first unlock. then android started using file based encryption, which was used selectively, encrypting certain things so that they are accessible without an unlock.
the best way to figure it out is to set a new alarm 10 minutes from now, reboot your phone manually, and see whether the alarm goes off
I’m on S21FE and it does NOT.
Samsung does too but I’ve not set it up as such. Instead, it automatically locks the device from biometric unlocks every 24 hours until you login with your pin again.
GrapheneOS been had this feature, don’t let apple tell you they invented it.
Great software features should be available to all hardware, regardless of OS.
For sure I’m just joking about apple’s habit of taking a feature that has been around for YEARS and claiming they “innovated” it, usually after they strip it down a little no less (like in this case where it appears to be a setting users can’t access, but Graphene lets you turn it on/off or adjust the time between lock and reset.)
deleted by creator
Did they claim they innovated this feature? I wasn’t paying attention.
I assume so, it’s their typical MO and thus: The Joke™.
IMHO, the novelty of the feature isn’t what makes this headline worthy. This is noteworthy because of the scale. iOS is over a quarter of phones on earth, and in English speaking countries and Japan, you’re looking at numbers that are often over 50%.
This will impact a LOT more investigations than Graphene, and I imagine Apple will be back in court fighting cops who want to remove privacy and security features. Hopefully this stuff stands up to the autocrats coming into power in the states.
don’t let apple tell you they invented it.
Why always the knee-jerk anti-apple reaction even if they do something good?
FYI: Apple isn’t telling anyone they invented this. In fact, they didn’t even tell anyone about this feature and declined to comment after it was discovered and people started asking questions.
Android in general has it, not just you.
All six GrapheneOS users should be proud that the developers of their phone software are genius inventors!
Gotcha. We’re almost twice as many.
I’m looking forward to joining the dozens with my nexto phone v

And most of them are in this thread.
Judging by the downvote count, I was off by 2x. My apologies to the community!
(For the record, I have nothing against GrapheneOS, but also no use for it)
deleted by creator
There is no shortage of reasons to dislike Apple. This isn’t one of them.
There is a scene in Mr Robot where Darlene is able to do a full wipe on her phone without even looking at the screen.
I wish I was that good.
I want a way that I can trigger this from the main lock screen without unlocking the phone.
Like a specific pin you have to enter twice to trigger the full wipe.
GrapheneOS has this. I believe it’s called a Duress PIN.
I’ve set mine up so that entering my PIN backwards will nuke it. At which point I can ask for my phone back.
At which point you will be taken to a dark room downstairs and 3 cops will testify they tried very hard to stop you from violently and repetitively throwing your head at their baton in a menacing manner which made them fear for their life.
speaking of that.
this can wipe your phone on a trigger, or lock it with a different code, or send a broadcast message that other apps can act on: Wasted (Lock a device and wipe its data on emergency) https://f-droid.org/packages/me.lucky.wasted/
this reads the screen to see if you have used a special unlock code: Duress (Duress password trigger) https://f-droid.org/packages/me.lucky.duress/
read the app description of both, there’s important information
It also let’s you install a fake icon for some normal looking app like Threema. When you tap the app it factory resets the phone.
yeah they are pretty good apps! basically a must-have for protests, if you bring a smartphone. maybe for traveling too, in case it’s stolen
Do not under any circumstances bring your cell phone, dumb or not, to a protest.
Memorize important numbers, writing them in your arm if necessary.
Answer all questions with “I assert my fifth amendment right and will not answer any further questions without my attorney.”
I can see these apps being good for traveling, in case of a stolen phone, but for protests I’ve almost always heard that you should bring a burner phone.
if the burner phone is a cheap smartphone, it could still be helpful
Best you can do is auto wipe after 10 failed pins.
I feel that a lot of the hate for Apple is not fully warranted. Contrary to Google or Facebook, their business model is not built on collecting your personal data. They are extremely overpriced, but deliver good quality - I am using my first iPhone for more than 4 years now, I never had and Android last nearly that long.
In my experience, that’s true, too. I won’t complain about build quality.
I’m currently in a weird thing with Apple. I’ve been using Macs since ‘07 and iPhones since ‘10, and while they make absolutely incredible hardware, I’m sick of how much they rip off their customers, and I’m sick of being able to see the ways in which they adapt software to push you towards the thing that makes them the most money.
As a result I have an M2 MacBook which is the best laptop I’ve ever owned, and I’m close to putting Asahi on it to see if I can use that flavour of Linux as a daily driver. Come February, when my iPhone 13 mini is due for upgrade, I’m giving serious consideration to picking up a used Pixel 8 so I can use Graphene instead.
On a pixel 8 running graphene right now, I love it.
Did you switch to it from Android or iOS? Because as someone who’s only used iOS since 2010, I imagine it’ll be one hell of a shock.
Android. It might be a shock, but it’s great once you get used to it. I completely degoogled and went with apps that don’t spy, which was the hardest part, but you could set up a separate user profile for spyware stuff like snapchat or whatever. It might be beneficial to go ahead and get one, flash it, and use it with wifi or a prepaid sim for a bit while you still have your regular phone as a backup/main if you’re worried about the transition.
The best thing apple ever did was convince you they don’t collect and sell your data like the other tech giants. You think they’re a trillion dollar company by their hardware alone?
Apple is just as shit they just make sure folks don’t realize it
Pssst, apple collects your personal data, and like google they “don’t sell it,” instead they use it to build profiles on their users and then go to ad agencies and say “Ok give us money and we’ll serve your ad to X demographic.”
Does Apple serve ads? Not that I am aware of. I suppose their podcast player supports podcasts that have dynamic ad breaks but I honestly have no idea whether Apple is the one selling that ad space or the platform hosting the podcast is.
They have services that claim to, but tbf I don’t use apple products and I block ads like I’m spraying for roaches, so I’m just taking apple at their word.
Here’s a screencap from the TLDR of their terms of service I posted a link to, says right here “This service may use your personal information for marketing purposes” so…
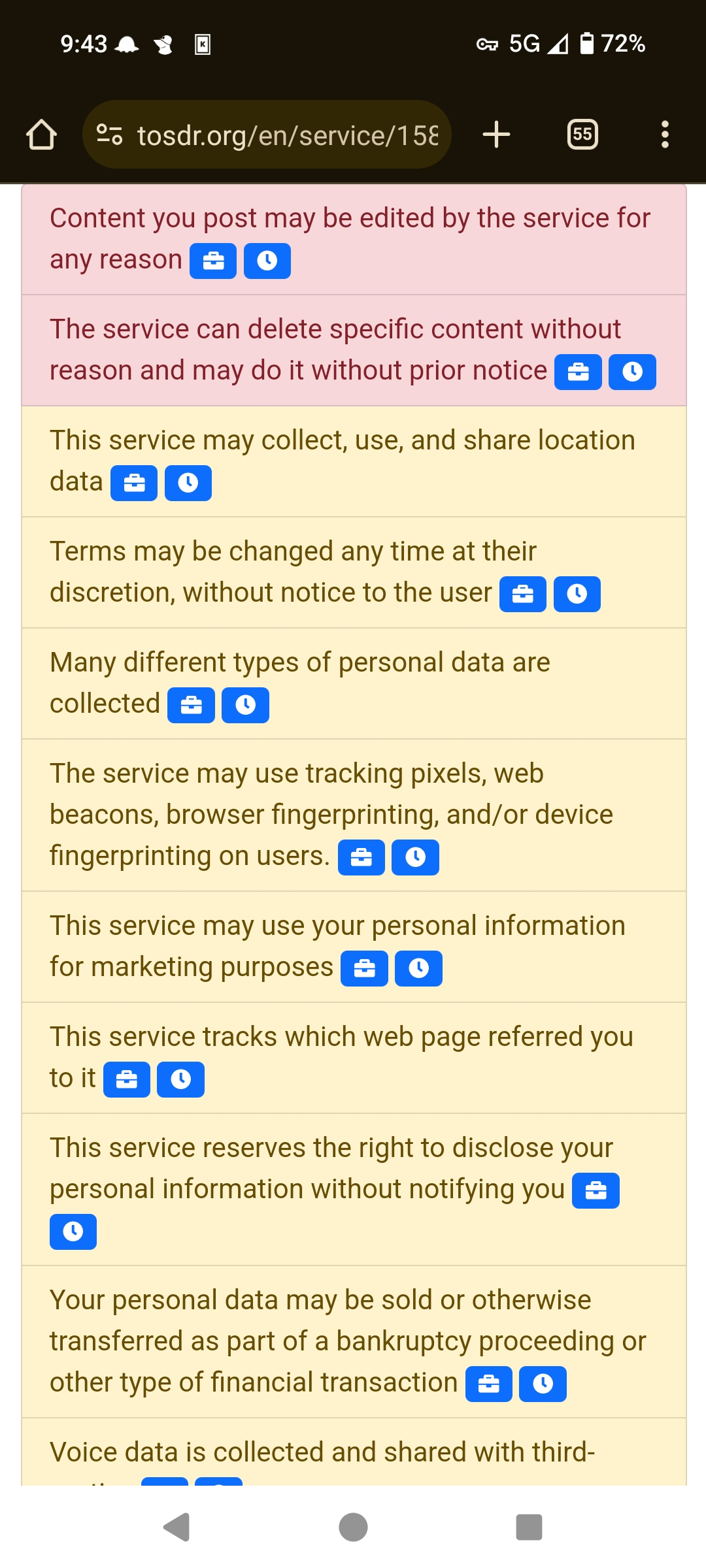
As a member of the intelligence community, I can almost guarantee that this is directed at the increased use of Cellebrite UFED hardware, specifically putting the device back into BFU mode, which removes cryptography-related memory allocations. This is also why you’re asked for your password instead of face or fingerprint upon reboot.
I don’t know how Cellebrite is a legally operating company. Their entire business model is a violation of the computer fraud and abuse act.
No that’s only for when poor people do it
Cellebrite is developed in Israel, a country that legally shouldn’t even exist, and is known for genocide, crime, espionage, manipulation and propaganda, more war crimes, illegal settlements, using their intelligence agency to assassinate political opponents abroad, etc.
The so-called “only democracy in the middle east”
They have offices in the US
Cellebrite isn’t American.
They have offices in the US
When the government does it, it’s not illegal.
I’m sure the CFAA has an explicit exception for law enforcement anyway. Laws always do.
Cellebrite themselves do it. The will unlock phones as a service.
Which is great, because you can’t warrant a password.
I am also an intelligent individual in a community! High five
It also wasn’t a quiet patch, users had to opt in.
As a member of the Intelligence community, please go find another job and stop harming people. Thanks.
Don’t be naive
The phrase “as a member of the intelligence community” is not the same “as as a mother”.
Assuming it is true, always a caveat on the internet, It would actually give them a unique perspective into the situation rather than just using it as a catch-all excuse for Karen’s to be an uninformed twit.
deleted by creator
IC refers to State actors. They don’t help people.
I assume being blown up by a terrorist is not everyone’s idea of a good time. Oh indeed anyones.
We have laws that prevent such things. We don’t need mass surveillance, just traditional LE
You’re right, we can make terrorism a crime. That will stop them.
When they say they’re part of the intelligence community, it seems highly likely that they are spying on their own citizens, or at least that’s what their job entails.
The way this article is framed sounds like bullshit to me. 18.1 was released less than 2 weeks ago. Any phone running this version of iOS would have had to already been in custody and somehow upgraded to this version, or otherwise brought into custody very recently—too recently for this to have already posed such a problem that law enforcement is “freaking out” and reporting it to the media.
Don’t they auto update the OS when connected to a charger? But even then, that would have triggered a reboot already.
This is the easiest thing for people with money, and motivation to avoid happening.
Remove the sim card if it’s an older device, use a Faraday cage (your microwave is one) or a jammer. If you are the government you can also tell the telecom to block the phone from connecting
Police may be leaving phones online in case it continues receiving relevant evidence (texts, emails, etc).
I think you’re seriously overestimating the technical prowess of the average law enforcement officer…
The ars article mentioned 18.0 had a bug that caused random reboots so it might’ve been mostly that
iOS has auto update for a while and iOS users update their devices more often than Android. 2 weeks is not a long time for adoption of new version for iOS.
The way this article is framed sounds like bullshit to me. 18.1 was released less than 2 weeks ago. Any phone running this version of iOS would have had to already been in custody and somehow upgraded to this version, or otherwise brought into custody very recently—too recently for this to have already posed such a problem that law enforcement is “freaking out” and reporting it to the media.
A non-insignificant amount of people have been running the public betas because of Apple intelligence, RCS / iMessage toys, UI customization, etc. For example, MixPanel reported about 2% of the iOS install base running 18.0 before 18.0’s launch. IMHO, that’s pretty crazy for a beta OS.
Thank you Apple, right side of history here, fuck fascist pigs
Wouldn’t that disrupt the usage of a phone as a server?

oh fuck I can’t stop laughing
You joke but people do that. I’ve seen people repurpose their old android phones to host small services on their home networks. I won’t comment on how reasonable it is because battery, but it’s a thing.
Literally no difference between a low power SOC RaspberryPi or a fucking phone which is the same thing with a built-in display.
What exactly is the phone fucking?
Mostly my mental health.
To shreds we all say. Hope you are well though.
Except the price, which is much lower for the SBC, way much lower if one uses one of the lower end Orange Pi or Banana Pi SBCs.
Also you can put Linux on the SBCs (which always come unlocked) hence do way more with them as servers than if one has to use Android as the OS.
I mean, I can get it if people with the technical chops, love for technical challenges and an old and pretty much worthless Android phone, configure it as a server if only because “why not?!”, but it’s not exactly a great option considering that a 40 bucks SBC can do the same, only better, more easily and with far more possibilities (given that it will be running Linux rather than Android).
PS: Actually somebody below mention mobile network connection, which, thinking about it, would be a good reason to use an old Android phone as a server since it has built-in support for 3G (unless it’s quite old) whilst the SBC needs it add to it which might be a problem for the cheaper SBCs (just wondering about how I would get around to do it, I think you need to connect a USB dongle to it and it has to be something compatible with Armbian Linux)
When you consider the price of a used android (ie. Oneplus 6T for $80 on ebay) and compare it spec for spec with a raspberry pi, it’s actually a really good deal. Like you get:
- Built in backup power supply (battery)
- 8-core power-efficient CPU (SDM845)
- Embedded sensors (microphone, magnetometer, gyro)
The way I set mine up is to run the server directly on Android using Termux, having an app autostart Termux on boot, and making sure to disable battery optimizations on the app. And then I just had the phone always plugged into the outlet to maintain the battery (and of course android would just trickle charge / disable once full charged).
Of course this isn’t perfect because you still have much more variability in play (at the OS level) than an RPi (along with not having a standard environment like debian unless you use proot), but it overall is a very powerful setup that works quite well.
I don’t think the sensors really matter for a server but the rest makes some sense.
Still, 80 bucks will buy you quite literally a Mini-PC (a really crummy one, granted) which can run more server tasks because it has as much or more memory and storage and isn’t hindered by there being an Android OS layer there doing nothing useful, and which is absolutelly and 100% under your control because it boots into your OS of choice.
Half than that will buy you a crummy SBC which probably de facto has as much capability to run server tasks as that Oneplus (it’s weaker but doesn’t have Android there eating up resources) though in my experience those things tend to be a bit finicky.
I don’t think it’s actually worth it to spend $80 on an used phone to use as a server (unless you do need UPS-like features or built-in mobile nertwork access) since you quite literally have better options brand new for that money, but if you have one around it can make sense even if it’s a bit more work getting it going and is not fully under your control (unless we’re talking about something jailbroken where you can install Oxygen or Lineage on, so a Pixel would probably be a better choice).
That said, there is a certain technical elegance in the whole notion of repurposing an Android Phone to be a home server.
I really doubt an iOS update will affect people using android phones as servers.
It would affect me. I have an android virtual machine running on my iPhone.
could be a simple hot spot cell backup, like for reporting network outage, remoting in to certain devices, etc. essentially a secondary ISP to report on main isp and troubleshoot. especially if you have smart devices you could reboot remotely.
An iPhone is not going to be that. This isn’t phones in general doing this, just iPhones.
There are also far more efficient devices for that. More cost effective and more energy efficient.
I understand wanting to reuse old devices for something, but there’s a limit to what is power efficient as well.
I’m not saying someone should, but they could. and necessity trumps efficiency every time.
When it comes to iPhones, it’s not a shouldn’t, it’s a can’t.
The way iOS limits background process means you can’t. I develop for iOS apps for a living.
There’s still you should never under any circumstances allow unsupported devices to be exposed to the internet or any way. Because that’s how we get bot nets causing DDOS attacks.
my comment wasn’t about iPhones. and it is possible to do what I said with android
Except this whole article doesn’t apply to android. Android AFAIK has 0 announced plans to do this. So why is it a concern?
That’s it!! Now I will NEVER use an iPhone as a server. 😋
iPhone? Don’t these kill apps after a few minutes in background?
*seconds. KDE Connect dying the moment I turn off the iPad annoys me to this day.
It’s not that simple. iOS has a really sophisticated system for deciding which things to keep in memory and which to evict, and it only does that when it needs more resources. Choosing which apps to kill is based on how recently an app was used, how much of share resources are in use, how often the app gets used, if it’s doing background processing, and other more subtle signals.
Usually if people notice apps being killed when in the background a lot it’s because one of the apps they’re switching to is using a lot of resources, which forces the eviction of other apps.
Interesting, tell me more please. I presume it requires loading a different OS image as standard iPhone/android OS images will pause apps and attempt to go into a deep sleep after a long enough period?
A phone server that is disconnected from cellular is already broken anyways.
On one hand, Fuck Da Police
On the other hand, Fuck Apple

Meanwhile security-oriented Android forks: “You didn’t do that?”
Actually, Graphene and Calyx have this feature. I believe graphene may have it on by default at 18 hours, but I do not know about Calyx.
Samsung phones have this as a feature too. I think it’s under device care
This is good but it isn’t quite the same thing. I want my phone to auto restart if I haven’t unlocked in for 12 hours.
Looks like the big difference is that this is on by default, it appears to get enabled when cops turn off internet access to prevent access to FindMy and remote lockdowns.
Oh nice
There’s also a feature to disable the biometrics for unlocking in general but to stay active to unlock apps (like bank apps or password managers). I like this because no matter what you can’t unlock my phone without the pin but I still get the convenience of using it for my app security
Calyx just copied the code from GrapheneOS, and I believe they still use the old GrapheneOS default of 72 hours
Well, if graphene turned it down to 18 hours, then they should as well. But I guess 72 hours is better than nothing.
lineageOS has this as well, as does divestOS but you have to set it
I was unable to find this on lineage 21 and I don’t think it would work as well on lineage anyway, since the vast majority of the bootloaders cannot be locked once lineage is installed, which would negate a lot of this I would think.
my bad, i just checked on lineage 21 again and i can’t find it, but i’m sure it’s on divestOS
I think this used to be possible with tasker, ironically though probably not anymore before of all Google’s restrictions on Android. (maybe if you have root)
GrapheneOS periodically (once a day or so) forces me to put in the passcode. If this isn’t a stock Android feature that’s another reason to use Graphene. It also has a “lockdown” button in the power button menu that forces the same behaviour.
Pretty sure it’s stock android, my phone does it every so often as well.
Sho does, annoys the hell outta me when it happens but I’d never disable that feature
And grapheneOS also reboots if it hasn’t been unlocked in the past 36 hours. Maybe the amount of time is different by default though, I might have changed it.
I have mine set to 18 hours
Why does rebooting it improve the safety or security of the phone?
When you first boot up a device, most data on that device is encrypted. This is the Before First Unlock (BFU) state. In order to access any of that data, someone must enter the passcode. The Secure Enclave uses it to recreate the decryption keys that allow the device to access that encrypted data. Biometrics like Face ID and Touch ID won’t work: they can’t be used to recreate the encryption keys.
Once you unlock the device by entering the passcode the device generates the encryption keys and uses them to access the data. It keeps those keys in memory. If it didn’t, you’d have to enter your passcode over and over again in order to keep using your device. This is After First Unlock (AFU) state.
When you’re in AFU state and you lock your device, it doesn’t throw away the encryption keys. It just doesn’t permit you to access your device. This is when you can use biometrics to unlock it.
In some jurisdictions a judge can legally force someone to enter biometrics, but can’t force them give up their passcode. This legal distinction in the USA is that giving a passcode is “testimonial” because it requires giving over the contents of your mind, and forcing suspects to do that is not legal in the USA. Biometrics aren’t testimonial, and so someone can be forced to use them, similar to how arrested people are forced to give fingerprints.
Of course, in practical terms this is a meaningless distinction because both biometrics and a passcode can grant access to nearly all data on a device. So one interesting thing about BFU vs AFU is that BFU makes this legal hair-splitting moot: biometrics don’t work in BFU state.
But that’s not what the 404 Media articles are about. It’s more about the forensic tools that can sometimes extract data even from a locked device. A device in AFU state has lots of opportunities for attack compared to BFU. The encryption keys exist, some data is already decrypted in memory, the lightning port is active, it will connect to Wi-Fi networks, and so on. This constitutes a lot of attack surface that hackers could potentially exploit to pull data off the device. In BFU state, there’s very little data available and almost no attack surface. Automatically returning a device to BFU state improves resistance to hacking.
Fun fact: in Australia we don’t have a bill of rights of any kind, so the cops can just force you to reveal your passwords. The maximum penalty for refusing is 2 years imprisonment.
Umm I forgot.
To the ASIO agent assigned to tracking my every online move:
- I didn’t see this comment.
- I don’t understand it.
- I would never do such a thing.
- I’m sorry this is what your life has been reduced to. Your patriotism is misplaced and you would be happier if you worked against the creeping surveillance state rather than for it. You know better than any of us how horrible it is, and you have the skills we need.
wtf
what!
Small comfort: they still can’t physically force you like they can with biometrics.
Honestly, as an american, I could live with watered down rights if it meant a more representative government
Oh yeah, just don’t read about what happens to our prime ministers when they attempt to defy the empire. Totes democracy we got over here.
Also, in the BFU state, iPhones at least, won’t allow any data connections through USB
It’s more complicated than that. It’s called USB restricted mode. The lightning port is always willing to do a minimal subset of the protocols that it supports in order to do smart charging. By default most of the protocols it supports are disabled in BFU state. In AFU state it gets more complex than that. Accessories that you’ve previously connected can connect for one hour after the device is locked. This helps keep USB restricted mode from being really annoying if you briefly disconnect and reconnect an accessory.
USB restricted mode can be disabled by a user option (Settings > [Touch / Face] ID & Passcode > Allow Access When Locked > Accessories) or by a configuration profile. Disabling it allows accessories to connect at any time, and generally lowers the security of your device. But in some cases that’s necessary, for instance when you use an accessibility accessory to use your device.
If USB restricted mode is a concern for you, you should consider Lockdown Mode (Settings > Privacy & Security > Lockdown Mode). This changes several settings on your device to make it much more resilient to attack.
Very informative. Thank you.
You mentioned the lightning port. Is there any difference with the newer phones with USB-C when it comes to these functions?
I’m glad you find this informative. It’s a topic that’s important to me both personally and professionally, and there’s a lot of wrong information out there. But the best and most reliable info is in the Apple Platform Security Guide, such as Activating data connections securely and Direct memory access protections for Mac computers.
In this topic I don’t think there’s any important difference between USB-C and lightning. Both form factors support a bunch of USB protocols as well as some Apple-only protocols, and both have USB restricted mode.
Great explanation. That was super insightful.
So even with BFU, does the iPhone not connect to the internet? I guess i hadn’t noticed it doesn’t.
Also are you still about to track via gps an iPhone that is in the off state? Just curious if there’s a lot of other vectors where the iPhone is still connected?
So even with BFU, does the iPhone not connect to the internet? I guess i hadn’t noticed it doesn’t.
Well, it’s complicated. Most of these topics are. In BFU state, an iPhone (or iPad with cellular) with an active SIM and active data plan will connect to the Internet. It won’t connect to Wi-Fi at all. If you have USB restricted mode disabled and the right accessory connected it will connect to an Ethernet network, but that may fail if the network requires 802.1x and the credential is not available in BFU state. Similarly if USB restricted mode is disabled you can use tethering to a Mac to share its network.
For location, there’s two mechanisms. One mechanism relies on directly communicating with the device, which only works if the device has network.
The other mechanism is the “FindMy network” which uses a Bluetooth low energy (BTLE) beacon to let other nearby devices detect it, and they report that to FindMy. It’s a great technology. The way it uses rotating IDs preserves your privacy while still letting you locate your devices. I know that this works when a device is powered off but the battery is not completely dead. I’m not sure if it works in BFU state… my guess it that it does work. But this is not networking. It’s just a tiny Bluetooth signal broadcasting a rotating ID, so it’s one-way communication.
Other than that, I’m not as sure how things work. I believe Bluetooth is disabled by default in BFU state, but I suspect users can choose to re-enable Bluetooth in BFU state to connect to accessibility accessories. I’m not sure about the new emergency satellite communication.
But one thing I know for sure is that Apple has world class security engineers, and one area they work hard to secure is devices in BFU state.
Wow ya that’s a lot of stuff to have to keep track of. Those security engineers are something else. I thought software security was already complex but iPhones or any phones sounds like its even more so
Once rebooted, you need to enter your PIN to unlock the phone (and the SIM as well). Before that it is not possible to unlock the phone with biometric credentials (face ID or fingerprint).
As far as I’m aware, police can force you to hand over your biometric credentials (they can hold the phone to your face to unlock it when you have face ID enabled, or can move your finger to the fingerprint sensor). But they can’t force you to reveal the PIN number.
Yep: but they can’t force you to give them the password because of 5th Amendment protections from self-incrimination.
And even if they did have the right to tell you to give them the password, they don’t have access if you simply refuse to cooperate. They can get your fingerprints, face ID, or retina scan by force. They cannot extract information from your brain.
BTW: Lots if phones also have a “lockout mode” that can be enabled that will give you the option to lock it down to password-only without turning it off. It can be good for recording police interactions, because it will continue to record them while they can’t access the contents of the phone if they swipe it from you.
What about amputating the hand?
Yeah but that would imply they are bringing the phones to the person multiple times to use their face/finger, or they are keeping the phone active so it never locks, unless they are actively changing the settings to never lock somehow. Seems like an easier fix to just require you to enter your pin to change your lock setting to indefinitely.
Side note: the last time I was arrested the officer asked me if I wanted to reboot my phone or turn it off before handing it over so I knew they weren’t going to go through it. Was surprised
The more full reason is that the device is still encrypted prior to first unlock and is harder to extract any information from. As to what you said about police requiring you to enter your PIN, they can’t. You can’t be forced to reveal your passwords/PINs but they can legally force you to unlock biometrics (fingerprint/face ID)
I never said they could require you to enter a pin, my words are often a jumble. I was saying cops actually asked me if I wanted to restart or shut down my phone so I had peace of mind that they wouldn’t go through it.
I don’t know how the procedere would be executed, but I imagine that police could have the phone present during an interrogation and try to nlock it there (possibly by making you to look at the phone to unlock it, if the phone has been set up to unlock this way). Once unlocked, it would be sufficient to have a peek into the camera roll or messages, until the phone locks again. I don’t know about the law, but I can imagine that if a police officer had a look into your phone, even briefly, it may be held against the one who is being interrogated.
or can move your finger to the fingerprint sensor).
Good luck guessing which finger and on which hand. You have 3 tries before a password is required.
BFU (before first unlock) vs AFU (After first unlock)
Basically encrypted vs decrypted
As I understand it, even though after Reboot the OS looks like its in about the same state with the wallpaper and same password to unlock, the fact that it hasn’t been unlocked yet means that certain attacks don’t work as well. I don’t know why specifically. I think it’s because the attack may still work but doesn’t reveal any sensitive data because it’s just the ROM, wallpaper, sim, etc.
Most likely after rebooting but before unlocking the decryption key is not present in memory in plaintext.
How long until it reboots when inactive?
Chris Wade, the founder of mobile analysis company Corellium, told 404 Media that after the fourth day of a device being in a locked state, the device reboots.
Do two fucks make a right?


































