- 3 Posts
- 37 Comments

 2·8 days ago
2·8 days agoVLC is a great way to work with AppleTV, if you are willing to trade a few more clicks and less meta data for being free. It is by far the gold standard of being able to play anything.
The file format issue, plus the simple interface (especially for older less technically inclined) makes infuse worth the $100 lifetime cost (especially with family sharing).
What hardware are you using for your LibreELEC? Pi 3,4,5? With an external drive?

 2·8 days ago
2·8 days agoSelf-hosted is not a way to make things free. Just lower cost than subscriptions overall. Using the full *Arr suite, with Usenet, your own hardware, and client boxes gives the users better control of the content they watch, but requires a nominal input of users time (plus some technical expertise), as well as an investment of some money both one time and annually.
Infuse’s lifetime time cost, when viewed in light of the total reduction of subscription cost (and an improved control of content) is worth it. I would definitely not pay a monthly amount to infuse, although it’s possible.
So far as Jellyfin’s app… As its free, I have low expectations. They fact that the developers have paid Apple for the SDK and put it as a free app on Apple TV and iOS is incredibly kind of them. They have a fair amount of code to look after and open source developers rarely get enough love or money.

 231·8 days ago
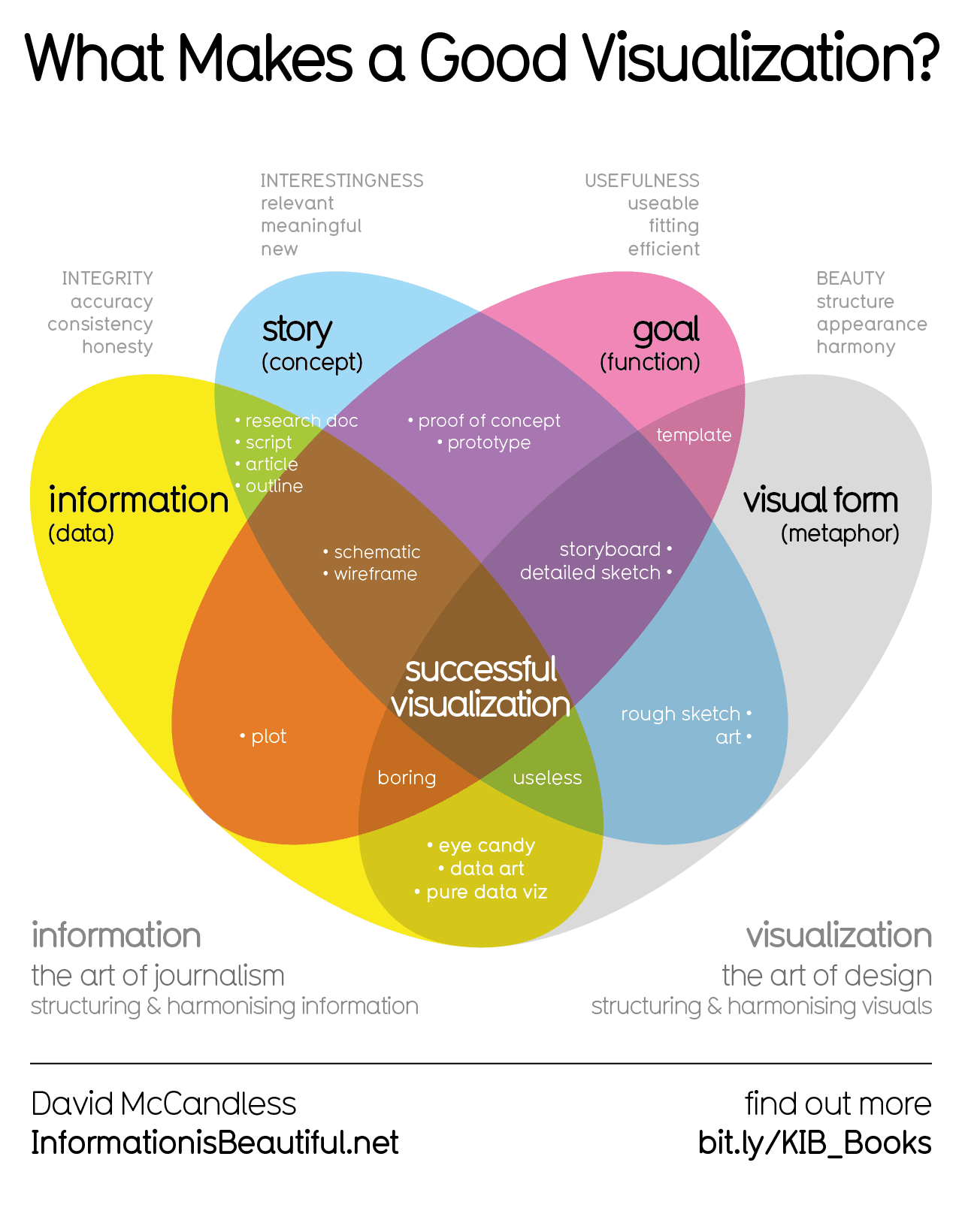
231·8 days agoDemocrats and independents who lean toward the Democratic Party are much more likely than Republicans and GOP-leaning independents to both use and trust a number of major news sources. These include the major TV networks (ABC, CBS and NBC), the cable news networks CNN and MSNBC, major public broadcasters PBS and NPR, and the legacy newspaper with the largest number of digital subscribers, The New York Times.
Republicans, meanwhile, are much more likely to distrust than trust all of these sources. A smaller number of the sources we asked about are more heavily used and trusted by Republicans than Democrats, including Fox News, The Joe Rogan Experience, Newsmax, The Daily Wire, the Tucker Carlson Network and Breitbart.
…

Each source’s placement on this chart is based on the average measure of U.S. adults who say they regularly get news from that source – taking into consideration both the party identification (Republican or Democrat, including leaners) and ideology (conservative, moderate or liberal) of respondents. Refer to the methodology for details.

 172·10 days ago
172·10 days agoI realize most will say kodi or android TV, but I have to say that Apple TV with Infuse (or Jellyfin) is really simple and reliable. I say that with the assumption that you mean a client, not the server. I would definitely put it on a NAS at minimum.

 6·12 days ago
6·12 days agoAlternative non-paywall link: https://archive.is/UZWXt

 6·13 days ago
6·13 days agoAt Seattle or Toronto’s price point, I think it’s likely a staff reduction by other means… That is unless the employees ignore it. https://www.inc.com/jessica-stillman/new-data-shows-workers-are-mostly-ignoring-return-to-office-orders/91202144

 4·13 days ago
4·13 days agoI can tell you after doing it on a house in Colorado, it’s a satisfying thing. It covers the sunniest hours, and we have batteries enough to get us past peak hours. I do wish we built it bigger and put more batteries in it, but that seems always true.

 7·13 days ago
7·13 days agoWhere is this graphic from? It’s awesome!

 5·14 days ago
5·14 days agoIf only it was this easy go find MH370. (And by easy I mean happening to look at apple maps sat images and find an anomaly.)
I think MH370 may be found some day, but our underwater autonomous drone game will have to move up a generation or two.

 6·16 days ago
6·16 days agoHighlighted by the OP, but
According to FFI, the Ukrainian battlefield experience reinforced Norway’s decision to prioritize artillery systems capable of achieving more than 40 kilometers in range and better survivability, and led to a reassessment of ammunition acquisition strategy, favoring volume and cost-effective accuracy improvements over limited high-cost precision rounds. The evaluation judged the acquisition to be economically sound and aligned with modern operational requirements, despite noting that long-term viability would depend on integrated force protection and continued ammunition procurement. The report applied the Concept program’s standardized methodology, assessing six criteria: productivity, goal achievement, secondary effects, relevance, viability, and economic efficiency.
This really is a concise description what artillery means to War now, and why.

 11·16 days ago
11·16 days agoIn an April sit-down, former transportation secretary Pete Buttigieg schooled Schulz and his co-hosts for believing in Trump’s promises.
I wanna see this.

 1422·16 days ago
1422·16 days agoFor those on iPhone and at any risk, ICEBlock app is potentially better, as it maintains more privacy.
The reason they don’t do android:
At ICEBlock, user privacy and security are paramount. Our application is designed to provide as much anonymity as possible without storing any user data or creating accounts. While we understand the desire for an Android version of ICEBlock, achieving this level of anonymity on Android is not feasible due to the inherent requirements of push notification services.

 121·20 days ago
121·20 days agoSome relevant quotes to summarize:
But the videos weren’t clear enough to identify the exact make or model of the dark four-door sedan. The detectives quickly obtained what are known as tower dump warrants, which required the major phone networks to provide the numbers of all cellular devices in the vicinity of 5312 Truckee during the arson. And they slung a series of so-called geofence warrants at Google, asking the company to identify all devices within a defined area just before the fire. (At the time, Google collected and retained location data if someone had an Android device or any Google applications on their cell phone.)
…
There were 1,471 devices registered to T-Mobile within a mile of the house when it ignited. Using software that visualizes how long it takes a signal to bounce from a cell tower to a phone and back again, Sonnendecker narrowed the list down to the 100 devices nearest to the house. One evening toward the end of August, detectives roamed the area around 5312 Truckee with a cell-phone-tower simulator that captured the IDs of all devices within range. That night, there were 723. Sonnendecker cross-referenced these with the 100 from earlier, eliminating the 67 that showed up on both lists and likely belonged to neighborhood residents who could be ruled out. That left 33 T-Mobile subscribers whose presence in Green Valley Ranch in the early hours of August 5 couldn’t easily be explained.
…
That’s when another detective wondered if the perpetrators had Googled the address before heading there. Perhaps Google had a record of that search?
… birth dates, and physical addresses for all users who’d searched variations of 5312 Truckee Street in the 15 days before the fire.
Google denied the request. According to court documents, the company uses a staged process when responding to reverse keyword warrants to protect user privacy: First, it provides an anonymized list of matching searches, and if law enforcement concludes that any of those results are relevant, Google will identify the users’ IP addresses if prompted by the warrant to do so. DPD’s warrant had gone too far in asking for protected user information right away, and it took another failed warrant 20 days later and two calls with Google’s outside legal counsel before the detectives came up with language the search giant would accept.
Finally, the day before Thanksgiving 2020, Sonnendecker received a list of 61 devices and associated IP addresses that had searched for the house in the weeks before the fire. Five of those IP addresses were in Colorado, and three of them had searched for the Truckee Street house multiple times, including for details of its interior. “It was like the heavens opened up,” says Baker.
In early December, DPD served another warrant to Google for those five users’ subscriber information, including their names and email addresses. One turned out to be a relative of the Diols; another belonged to a delivery service. But there was one surname they recognized—a name that also appeared on the list of 33 T-Mobile subscribers they’d identified earlier in the investigation as being in the vicinity of the fire. Bui.
…
Seymour’s defense argued that, in asking Google to comb through billions of users’ private search history, investigators had cast an unconstitutional “digital dragnet.” It was, they said, the equivalent of police ransacking every home in America. The Fourth Amendment required police to show probable cause for suspecting an individual before getting a warrant to search their information. In this case, police had no reason to suspect Seymour before seeing the warrant’s results. But the judge sided with law enforcement. He likened the search to looking for a needle in a haystack: “The fact that the haystack may be big, the fact that the haystack may have a lot of misinformation in it doesn’t mean that a targeted search in that haystack somehow implicates overbreadth,” he said
…
After a five-month wait that Sandoval remembers as “gut-wrenching,” the court finally ruled in October 2023. In a majority verdict, four judges decided the reverse keyword search warrant was legal—potentially opening the door to wider use in Colorado and beyond. The judges argued that the narrow search parameters and the performance of the search by a computer rather than a human minimized any invasion of privacy. But they also agreed the warrant lacked individualized probable cause—the police had no reason to suspect Seymour before they accessed his search history—rendering it “constitutionally defective.”
Because of the ruling’s ambiguity, some agencies remain leery. The ATF’s Denver office says it would only consider using a keyword warrant again if the search terms could be sufficiently narrowed, like in this case: to an address that few would have reason to search and a highly delimited time period. The crime would also have to be serious enough to justify the level of scrutiny that would follow, the ATF says.
…
Meanwhile, another case—in which a keyword-search warrant was used to identify a serial rapist—is now before the Pennsylvania Supreme Court. If the warrant is upheld, as it was in Colorado, their use could accelerate nationwide. “Keyword warrants are dangerous tools tailor-made for political repression,” says Crocker. It’s easy to envision Immigrations and Customs Enforcement requesting a list of everyone who searched “immigration lawyer” in a given area, for instance.

 13·22 days ago
13·22 days agoWithout paywall: https://archive.is/wkU2c
Summary:
The U.S. just handed the fossil fuel industry a big win. No matter how you look at it, that win will be short lived.
Electric vehicles are already displacing millions of barrels of oil per day, saving hundreds of millions of metric tons of carbon dioxide from entering into the atmosphere.
With or without U.S. support, the world will march on towards cleaner sources of energy.

 6·23 days ago
6·23 days agoImmediately following American air strikes, Iranian military officials jetted to Beijing to negotiate the purchase of J-10C fighter jets and AWACS from China.
Pakistan’s air force is equipped with Chinese-built fighters and missiles, and in a recent air battle against Indian forces shot down several top-line Western-built fighter jets and drones.
Chinese defense firms build equipment that is comparable or superior in quality, at considerable cost savings head-to-head against gear from NATO countries or Russia.
What’s more, other militaries are struggling to build weapons at all, given that supply chains for the most advanced munitions and systems run through China for rare earth metals, and the other BRICS countries for raw materials.
If China agrees to supply Iran, it will remake the military and diplomatic landscape of the Middle East, for decades to come
Interesting times… /s

 13·27 days ago
13·27 days agoYes I do!
They are working towards requiring it for all travelers.
Why: Think of this as a trial working towards full automation. They aren’t there yet and are not probably legally allowed to do so, but the idea is that you can be fully tracked like the British, Chinese, and other biometric adopted countries.
Prevention: Reliability and legality. As I mentioned I don’t think they can force it in the US for travel yet as it’s not legally allowed, nor is biometrics entirely reliable as is apparent when facial recognition fails.
 5·30 days ago
5·30 days agoAnyone have a link to the company who made it? My morning searchfu is failing me.
 3·1 month ago
3·1 month agoWhile the message is not entirely off, it’s worth realizing that polling approval numbers are all over the place. While Nate Silver might not peg it, be does at leas provide more polls which shows this:

As he says:
Now these differences aren’t too surprising. It’s normal for individual polls to disagree because of sampling error. But variation in how polls are conducted (whether they interview adults or registered voters, the variables they weight on, etc.) can make those differences even larger. For example, Trafalgar, InsiderAdvantage, and RMG all have Republican house effects while Ipsos tends to have a strong Democratic house effect. …
Inevitably, there’s a lot of disagreement from survey to survey, not just because of statistical variation but because pollsters have long had trouble pegging down Trump’s popularity — and often underestimated it.
Which is to say, polling is still more of an art.
This is not to dampen the delight too much, but reality is much more complicated than a poll.



As an old IT guy I empathize with the control of data. I have my array of self-hosted servers and love my CLI.
With that said, the older I get the less patience I have for hacking it together and supporting it. I still prefer privacy, and indeed Firecore Infuse is “Private by design” by their own statement. It’s not open source and I am not clear if it’s audited, but for as long as it lasts I’m happy friends and family less technically inclined have a simple easy familiar interface which I don’t have to support.
I will say I’m impressed A Pi4 works so well for jellyfin streaming. I guess it’s not transcoding, so it’s just a database and file share.